Worst Infection ever – CryptoLocker/Cryptorbit
Cryptorbit virus is another nasty ransomware software and acts as the Cryptolocker virus. More specifically when it infects your computer, it encrypts all the files in it. The bad news with these viruses is that, once they infect your computer, they encrypt critical files with strong encryption and it is practically impossible to decrypt them.
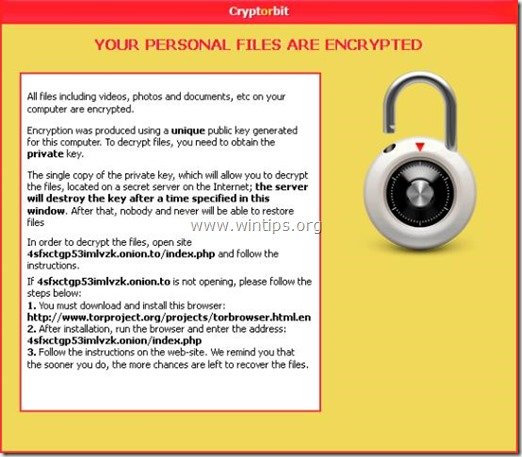
Specifically after the infection, the Cryptorbit Ransomware informs the user that “All files including videos, photos and documents on user’s computer are encrypted” and in order to decrypt them, the user must make a payment (of 500$ or 600$) in BitCoins, by following a specific procedure using Tor Internet Browser.
Cryptorbit and Cryptolocker are not viruses, they are malware. Falls PC offers protection against files from being encrypted, call for more information.
CryptoLocker/Cryptorbit FAQ’s
(Article from https://blog.richmond.edu/is-alerts/category/virus/)
How would I get infected?
- CryptoLocker/Cryptorbit is typically spread through email attachments and website drive-by-downloads. A “drive-by-download” occurs when websites infected with malware try to install the virus when you visit the site by exploiting a security flaw in either your browser software or Java software. Another method of transmission occurs when spoof emails that appear to be from companies such as UPS, FedEx, and DHL ask the user to open an attachment related to the information in the email. Once the user opens the attachment the virus is installed on the computer.
How can I avoid becoming infected?
- Do not open any email attachments from an untrusted or unverified source. Even when you know the source of the email, review the message thoroughly, and make sure that there is a clear reference to attached file. Don’t hesitate to contact the source and verify that they did send the attachment to you.
- Be careful while web browsing to not click on or open files from untrusted or unsure sites.
- Install anti-virus software on your computer, make sure it is running and keep the anti-virus software updated.
- Stay up-to-date on software patches.
How can I limit the damage of an infection?
- Backups are the most important part of preventing total data loss with a CryptoLocker/Cryptorbit infection. An offline backup such as an external hard drive will be able to restore earlier versions of your files if they become encrypted. It is important to keep your external drive unplugged from the computer when you are not actively backing up files as the virus will attempt to encrypt files on any connected storage device.
What do I do if I am infected?
- If you receive the CryptoLocker/Cryptorbit ransom screen disconnect your computer from the network to stop the spread of the virus.
- Do not pay the ransom. Paying the ransom only rewards the criminals and provides no incentive to cease their activities. It may seem like a small amount of money at the time but there is no guarantee that if you pay you will be able to decrypt your data.
- Consider enabling System Restore on Windows 7 or File History on Windows 8 to provide for an additional recovery option.
What computers are at risk?
- All computers using Windows XP 2, Vista, 7, 8, 8.1 and 10. This includes any Apple or Linux based computers running Windows in a virtual environment like Bootcamp, Parallels or VMware.
What does it do?
- CryptoLocker/Cryptorbit searches through a computer (and any attached networks or external storage devices) looking for specific common file types such as .doc, .docx, .xls, .xlsx, .pst, .jpg, etc…
- CryptoLocker/Cryptorbit then encrypts the files, rendering the files inaccessible to the user. The virus creates a pop-up screen that prompts the user to pay a ransom within 72 hours to decrypt the files. If the user does not pay within 72 hours, the files will be encrypted forever.
The full Cryptorbit (HOWDECRYPT) information message is as follows:
Cryptorbit
All files including videos, photos and documents on your computer are encrypted.
Encryption was produced using a unique public key generated for this computer. To decrypt files, you need to obtain the private key.
The single copy of the private key, which will allow you to decrypt the files, located on a secret server on the Internet; the server will destroy the key after a time specified in this window. After that, nobody and never will be able to restore files.
In order to decrypt the files, open site 4sfxctgp53imlvzk.onion.to/index.php and follow the instructions.
If 4sfxctgp53imlvzk.onion.to/index.php is not opening, please follow the steps below:
1. You must download and install this browser http://www.torproject.org/projects/torbrowser.html.en
2. After installation, run the browser and enter the address: 4sfxctgp53imlvzk.onion/index.php
3. Follow the instructions on the web-site. We remind you that the sooner you do, the more chances are left to recover the files.
IMPORTANT INFORMATION:
Your Personal CODE: 00000001-ED28BBCA”
Once Cryptorbit infects your computer, actually it starts to encrypt all files on your computer and then it sends the decryption key – known as “Cryptorbit Key” – to an online server. During Cryptorbit infection the malicious program also creates 3 files (HOWDECRYPT.GIF, HOWDECRYPT.HTML, HOWDECRYPT.TXT) on every folder that it encrypts its contents with instructions for payment and decrypting.
Cryptorbit (HowDecrypt) virus, actually doesn’t encrypt the whole file but only the first 512 bytes of the file header. After the encryption, it takes the encrypted 512 bytes and stores them at the end of the file header. As a result, the file becomes corrupted and appears unrecognizable to the system so you cannot open or access it anymore.
From our research on several sites, we can inform our readers that in some cases, the files remain encrypted, despite the fact that the user makes the payment. So make this decision (to pay to unlock your files) at your own risk.
MORE INFO
CryptoLocker/Cryptorbit is a new form of computer virus called “ransom-ware” that encrypts or “locks” files on a user’s computer and then attempts to extort money from the user in return for “unlocking” access to the users’ files.
Images like those shown below may appear as your desktop background or as an image saved to your desktop.